The ongoing digital transformation (DX) and digital adoption of nascent technology are accelerating across sectors, leading to a proliferation of readily available tech solutions.
An example is the rise of bring-your-own-device (BYOD) initiatives and the consumerization of IT at large. These initiatives are considered an acceptable form of shadow IT and have proven beneficial as they allow employees to find and implement technology solutions that are most efficient without the bureaucratic red tape that can slow down innovation.
As such, the lines between using personal and work-sanctioned technology (e.g., smartphones, software, devices, etc.) to fulfill workplace obligations are steadily blurring.
This embrace of consumer technology within the workplace has led to unintended consequences, most notably in the potential for rogue IT to arise – the use of unsanctioned technology in a business environment.
Research from Purplesec found that the number of security breaches in enterprise organizations has increased by 27.4% annually. This, compounded by the fact that 97% of companies have experienced cyberattacks involving mobile threats, underscores the risks associated with rogue IT.
As such, the question of rogue IT sits firmly within the purview of CIOs and CISOs, who must weigh the benefits and risks of rejecting, regulating, or embracing it. The latter is emerging as the preferred way to safely accommodate public and personal networks within business environments.
This article will examine the growing concern of rogue IT in enterprise companies and how it can impact an organization’s security and data privacy.
We’ll discuss who is ultimately responsible for fixing the issue and provide readers with the best practices for dealing with rogue IT and maintaining a balance between security and innovation.
What is Rogue IT?

Rogue IT, also known as shadow IT, refers to the use of hardware, software, or other technology solutions within an organization without the approval or knowledge of the IT department.
These unapproved technologies are typically brought in by employees who need to use unconventional solutions to complete their work faster or more efficiently. With the rise of cloud computing and mobile devices, rogue IT has become more prevalent. Employees can now easily download apps and use cloud services without IT approval.
While shadow IT can benefit businesses and help employees leverage technology conveniently, unmitigated rogue IT can lead to a deliberate breach of company policies.
In working environments where smartphones, the Internet of Things (IoT), and wearable devices are commonplace, the risk of cybersecurity threats and data breaches via rogue IT is significantly increasing.
It’s easier for employees to cut corners and opt for the quick-fix tech solution of using an unsanctioned domain when proprietary IT doesn’t quite cut it. It could be that the in-house system is temporarily down, or an employee is unaware of the implications of sharing data outside the network; rogue IT is bound to occur – intentional or not.
However, this can lead to security risks, compliance issues, and data breaches, as rogue IT solutions are subject to different standards and protocols than approved solutions.
Why is rogue IT dangerous for enterprise companies?
Rogue: a word that evokes a sense of mystery and intrigue, but when it comes to enterprise companies, it’s a word that carries far more sinister connotations. The actions of rogue employees within a company can have devastating consequences – from data breaches and intellectual property theft to financial loss and reputational damage.
In an enterprise context, the term “rogue” typically refers to an employee who acts outside of the established policies and procedures of the organization. These individuals may take risks that could compromise the security and stability of the company, often motivated by personal gain or misguided intentions.
A recent study by Kaspersky revealed that 52% of businesses hold their employees as the primary weakness in IT security. This was due to their careless actions, which put IT security strategies at risk, posing a significant threat to the safety of business operations.
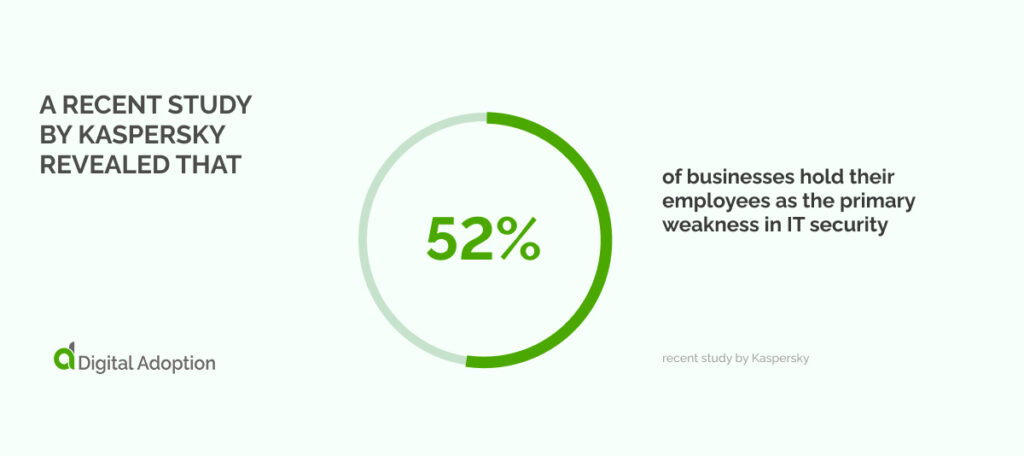
The danger of rogue behavior lies in the fact that it can often go undetected until it’s too late. Advanced technologies and relentless cyber attackers create a complex and ever-evolving threat landscape. Enterprises must remain vigilant in identifying and addressing rogue employees to reduce the risk of data breaches and other malicious activities.
Enterprises must actively guard against the threat of rogue behavior, which has the potential to inflict serious harm on a company’s bottom line and reputation. Proper policies, training, and security measures must be implemented to address the risk of rogue activity, ensuring the safety of the company and its stakeholders.
Who is responsible for fixing the rogue IT?
The responsibility for fixing rogue IT falls on many individuals in an enterprise, especially Chief Information Security Officers (CISOs) and Chief Information Officers (CIOs).
As the CISO, they are responsible for ensuring a secure IT environment free from unauthorized access and data leaks. They must continuously monitor the enterprise IT infrastructure and determine where improvements need to be made to prevent rogue IT activities.
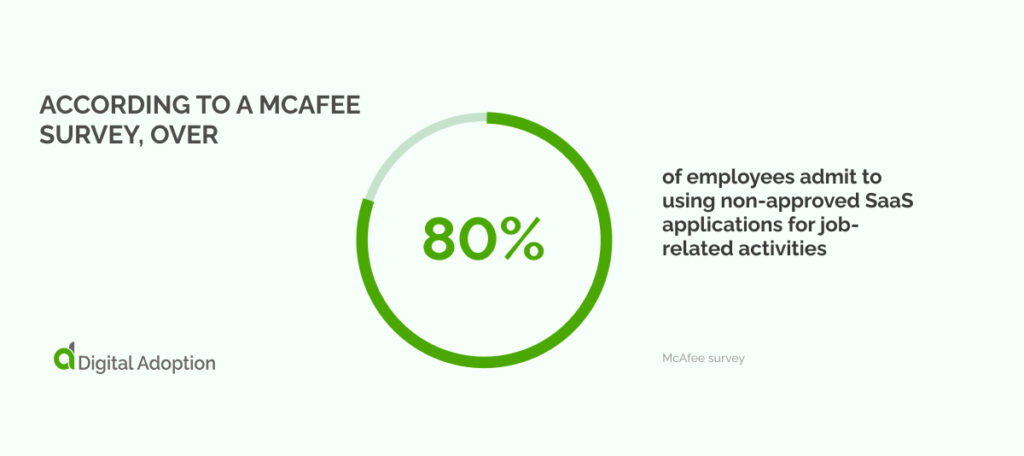
According to a McAfee survey, over 80% of employees admit to using non-approved SaaS applications for job-related activities.
This fact is particularly alarming when paired with results from a recent BetterCloud study revealing that organizations use an average of 80 SaaS applications. Enterprise organizations tend to utilize even more, with an average of twice as many SaaS apps.
The chief information officer (CIO) also plays a significant role in fixing rogue IT. Those in this executive role ensure that the enterprise IT systems perform optimally and meet the company’s technology needs. They must work with the IT security team to evaluate the risk of rogue IT activities and collaborate to devise an effective plan to mitigate those risks.
Effective communication and collaboration between the CISO and CIO are critical to resolving rogue IT activities. The CISO can provide valuable insights into potential security threats, while the CIO can offer technological solutions to address those threats. Together, they can create a comprehensive plan for detecting and preventing rogue IT activities.
While CISOs and CIOs are responsible for fixing rogue IT, it is essential to remember that addressing the problem is the responsibility of the entire enterprise.
Everyone, from managers to employees, plays a role in identifying and reporting rogue IT activities. With a collaborative effort and shared responsibility, enterprises can protect their IT systems and prevent rogue IT activities from happening in the first place.
Dealing with Rogue IT: Best Practices
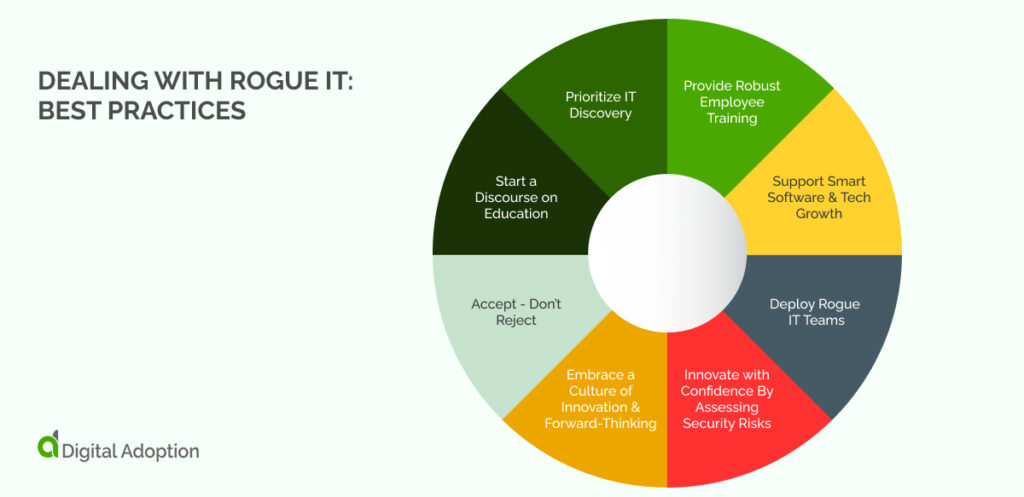
- Accept – Don’t Reject
While rejecting or eliminating rogue IT instances may be tempting, doing so can be counterproductive. A better approach is to accept that rogue IT is unavoidable and instead focus on strategies to manage it.
By doing so, businesses can tap into the potential of rogue projects while ensuring security, compliance, and productivity. Rather than stifling innovation or creating unnecessary barriers, embracing rogue IT can lead to a more agile and adaptive business environment.
- Start a Discourse on Education
One of the best practices for addressing rogue IT is to spark educational discourse among employees and stakeholders.
This approach promotes awareness and understanding of the potential risks and dangers of using unauthorized IT systems or tools. By educating employees and stakeholders, organizations can help them understand the value and importance of following proper IT protocols and procedures.
As the leaders of your organization’s technology initiatives, CIOS must understand the potential value of rogue projects.
Instead of ignoring or suppressing these initiatives, educating and expressing their potential value to the organization can be key. Here are a few ways to approach the situation:
Acknowledge the initiative: Rather than ignoring or taking an adversarial stance towards rogue projects, acknowledge the initiative and its motivations. This approach will promote a positive conversation around the issue.
Understand the goals: Take the time to understand the goals and scope of the initiative. By doing so, you’ll be able to identify potential overlaps, divergences, and opportunities to align IT goals with those of the initiative and provide support when warranted.
Encourage collaboration: Collaborate with the project champions and encourage them to partner with IT to find common ground. This approach may reduce the risk associated with rogue initiatives and promote the integration of cutting-edge technologies into existing IT infrastructure.
- Prioritize IT Discovery
IT discovery is vital for any organization engaging in safe data exchange.
Employees deploying their IT solutions can cause risks to the organization – including those sanctioned and rogue.
Prioritizing IT discovery can help mitigate risks by gaining visibility into the IT solutions and monitoring them.
The first step is to establish a comprehensive IT inventory, including all IT solutions, and maintain it regularly. Invest in discovery analysis tools and technologies that help discover and monitor IT solutions, categorize them, track usage and access, and monitor compliance with regulations.
By prioritizing discovery, the organization can mitigate risks associated with rogue IT, maintain a secure and compliant infrastructure, and leverage new opportunities with minimal risk.
- Provide Robust Employee Training
Investing in employee software training can also greatly reduce the risks of unmitigated rogue IT. Employees often use unauthorized mediums, such as personal email or messaging apps, because they need to be aware of the approved communication channels within the workplace.
By providing thorough training on the approved software and systems, you can help to prevent employees from seeking alternative methods.
Another approach to ensuring that employees use approved channels is by utilizing a Digital Adoption Platform (DAP). Digital Adoption Platforms (DAPs) are specialized software solution that helps companies facilitate their digital transformation efforts.
These platforms provide a range of tools and resources that allow users to adopt and leverage digital applications without extensive coding knowledge or skills.
Our data reveal the earning revenue of select companies in 2022. Walkme has emerged as the top earner, generating $178 million in revenue so far. The second position is claimed by Pendo, with a respectable $100 million in revenue.
By providing thorough software training or using a DAP, you can ensure that employees are aware of the approved methods for communication and properly equipped to use the software and systems they need to do their job.
- Support Smart Software & Tech Growth
One of the best practices for dealing with rogue IT is to support smart software.
As more and more employees turn to unapproved applications and programs, providing them with a viable option that meets their needs and the organization’s security policies are important.
Smart software is designed to address the specific needs of businesses and their employees. These programs offer reliable and secure solutions that enable employees to do their jobs more efficiently and effectively. Additionally, smart software is built to integrate with other enterprise systems, so IT can easily control and manage it.
By supporting smart software, organizations can set an example for their employees and encourage them to follow best practices.
In addition to supporting intelligent software, facilitating new tech growth through non-IT teams is also important for quickly deploying solutions that meet business needs, which can speed up cost reductions and optimize resource efficiency.
- Deploy Rogue IT Teams
CIOs must re-think their IT strategies and design new ones that integrate capital IT with non-IT team projects.
This will require embracing an innovative mindset to leverage projects outside traditional IT teams to maximize technological resources and create new value.
Deploying rogue IT teams may prove to be beneficial for organizations. These are small, autonomous teams of developers and IT professionals who work on projects without the direct involvement of the CIO or IT department. Rogue IT teams can move quickly and develop solutions that may not have been possible through traditional IT channels.
However, rogue IT teams should be controlled and monitored to avoid potential security risks and ensure their solutions align with the organization’s overall IT strategy.
- Innovate with Confidence By Assessing Security Risks
To evaluate the adoption of new technologies or innovations, organizations can assess the magnitude of security risk associated with the rogue project against the potential benefits it can bring to the organization. By doing so, organizations can make informed decisions about pursuing the technology.
This approach allows organizations to balance new technology’s potential risks and benefits and make decisions aligning with security strategies.
By assessing security risks and proactively dealing with rogue IT, organizations can innovate confidently, knowing they are taking the necessary steps to secure their systems and protect their sensitive data.
This not only helps to prevent data breaches and other security incidents but can also contribute to a culture of security awareness and responsibility across the organization.
- Embrace a Culture of Innovation & Forward-Thinking
Effective management of rogue IT requires a proactive approach to integrating new ideas and solutions to avoid potential threats.
In this context, embracing a culture of innovation and forward-thinking can help organizations develop a proactive IT security environment that addresses potential issues before they arise.
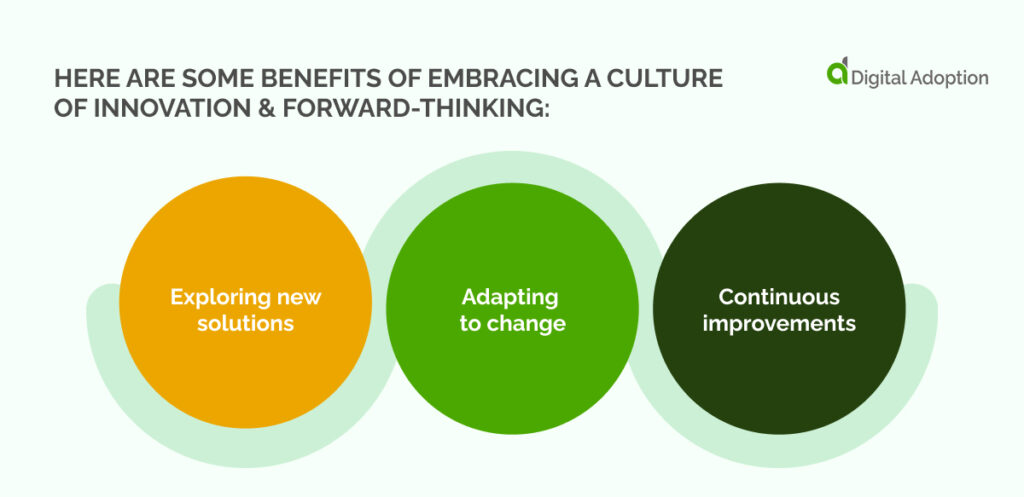
Here are some benefits of embracing a culture of innovation & forward-thinking:
Exploring new solutions: When an organization has a culture of innovation, it encourages employees to constantly explore new and better ways of doing things. This mindset can lead to discovering new solutions for tackling rogue IT.
Adapting to change: Innovation requires flexibility and adaptability, which can be crucial when dealing with rogue IT. A culture of innovation can help an organization quickly adjust to changing circumstances and stay ahead of potential threats.
Continuous improvements: By continuously exploring new ideas, an organization can identify areas for improvement and make positive changes. This can help prevent rogue IT from becoming a long-term problem and improve overall IT security.
Rogue IT: Balancing Security and Innovation
Rogue IT emerges as a precarious consequence of the ubiquity of personal technology at work. As organizations look to harness technology to drive innovation, CIOs face the challenge of balancing the need for innovation with the imperative to maintain cybersecurity standards.
In a world that has been moving increasingly toward agile work and remote methodologies, IT teams are being stretched thin while simultaneously facing a growing list of security threats.
Yet, innovation cannot be sacrificed in the name of security. Rather, CIOs should balance innovation and security by embracing digital transformation advances while also being mindful of security considerations.
Balancing innovation and security can seem daunting, but organizations that successfully navigate this challenge will be best positioned to thrive in today’s dynamic business environments. As cybersecurity threats continue to evolve, it will be critical for CIOs to remain vigilant and adaptable in their approach to securing their organizations’ data.
Ultimately, those CIOs who can strike the right balance between security and innovation will be the ones who can achieve long-term success. This requires a thoughtful and strategic approach that considers both immediate needs and the broader strategic vision of the organization.
Ultimately, the key to success lies not in sacrificing innovation for the sake of security but in sacrificing security for the sake of innovation. Rather, success requires a balance between these two crucial components of organizational success.





![18 Examples of AI in Finance [2025]](https://www.digital-adoption.com/wp-content/uploads/2025/06/18-Examples-of-AI-in-Finance-2025-300x146.jpg)
![14 Examples of AI in Manufacturing [2025]](https://www.digital-adoption.com/wp-content/uploads/2025/06/14-Examples-of-AI-in-Manufacturing-2025-300x146.jpg)
![29 Examples of AI in Education [2025]](https://www.digital-adoption.com/wp-content/uploads/2025/06/29-Examples-of-AI-in-Education-2025-300x146.jpg)
![15 Examples of AI in Retail [2025]](https://www.digital-adoption.com/wp-content/uploads/2025/06/15-Examples-of-AI-in-Retail-2025-300x146.jpg)



![18 Examples of AI in Finance [2025]](https://www.digital-adoption.com/wp-content/uploads/2025/06/18-Examples-of-AI-in-Finance-2025.jpg)
![14 Examples of AI in Manufacturing [2025]](https://www.digital-adoption.com/wp-content/uploads/2025/06/14-Examples-of-AI-in-Manufacturing-2025.jpg)